-
Nick Saban Sends Subtle Warning to Kalen DeBoer, Alabama - 10 mins ago
-
Texas Coach Steve Sarkisian Reportedly Interested in NFL Jobs, Including Titans - 15 mins ago
-
‘Blind Side’ star credits God with saving his life, losing 200 pounds - 43 mins ago
-
India’s top court wanted Delhi’s stray dogs gone, but it may have worsened the issue - 48 mins ago
-
How to Watch South Florida vs Memphis: Live Stream NCAA College Football, TV Channel - 49 mins ago
-
College Football Week 9 Live Updates, Scores: UCLA-Indiana, Ole Miss-OU, More - 57 mins ago
-
Commentary: As Trump blows up supposed narco boats, he uses an old, corrupt playbook on Latin America - about 1 hour ago
-
Sylvester Stallone reveals Hollywood abandoned him for nearly a decade - about 1 hour ago
-
Toddler’s Reaction To Mom’s Accidental Home Birth Captured on Camera - about 1 hour ago
-
Russian museum’s tribute to North Korean soldiers in Ukraine - 2 hours ago
New phishing scam targets university staff payroll to steal paychecks
NEWYou can now listen to Fox News articles!
Phishing scams target every kind of institution, whether it’s a hospital, a big tech firm or even a fast-food chain. Educational institutions aren’t an exception, especially in 2025, when attackers are actively directing their efforts toward them. Universities across the U.S. are facing a new type of cybercrime where attackers are targeting staff to hijack salary payments. Researchers have discovered that since March 2025, a hacking group known as Storm-2657 has been running “pirate payroll” attacks, using phishing tactics to gain access to payroll accounts. Let’s talk more about this attack and how you can stay safe.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide — free when you join my CYBERGUY.COM. newsletter.
SCAMMERS NOW IMPERSONATE COWORKERS, STEAL EMAIL THREADS IN CONVINCING PHISHING ATTACKS
How does the university payroll scam work
According to Microsoft Threat Intelligence, Storm-2657 primarily targets Workday, a widely used human resources platform, though other payroll and HR software could be at risk as well. The attackers begin with highly convincing phishing emails, carefully crafted to appeal to individual staff members. Some messages warn of a sudden campus illness outbreak, creating a sense of urgency, while others claim that a faculty member is under investigation, prompting recipients to check documents immediately. In some cases, emails impersonate the university president or HR department, sharing “important” updates about compensation and benefits.
Phishing scams are evolving fast and now universities have become prime targets for payroll theft. (Kurt “CyberGuy” Knutsson)
These emails contain links designed to capture login credentials and multi-factor authentication (MFA) codes in real time using adversary-in-the-middle techniques. Once a staff member enters their information, the attackers can access the account as if they were the legitimate user. After gaining control, the hackers set up inbox rules to delete Workday notifications, so the victims do not see alerts about changes. This stealthy approach allows the attackers to modify payroll profiles, adjust salary payment settings and redirect funds to accounts they control, all without raising immediate suspicion.
COLUMBIA UNIVERSITY DATA BREACH HITS 870,000 PEOPLE
Hackers are exploiting universities at scale
The hackers don’t stop at a single account. Once they control one mailbox, they use it to spread the attack further. Microsoft reports that from just 11 compromised accounts at three universities, Storm-2657 sent phishing emails to nearly 6,000 email addresses at 25 institutions. By using trusted internal accounts, their emails appear more legitimate, increasing the likelihood that recipients will fall for the scam.
To maintain access over time, the attackers sometimes enroll their own phone numbers as MFA devices, either through Workday profiles or through Duo MFA. This gives them persistent access, allowing them to approve further malicious actions without needing to phish again. Combined with inbox rules that hide notifications, this strategy lets them operate undetected for longer periods.
Microsoft emphasizes that these attacks don’t exploit a flaw in Workday itself. Instead, they rely on social engineering, the absence of strong phishing-resistant MFA and careful manipulation of internal systems. In essence, the threat comes from human behavior and insufficient protection, not software bugs.
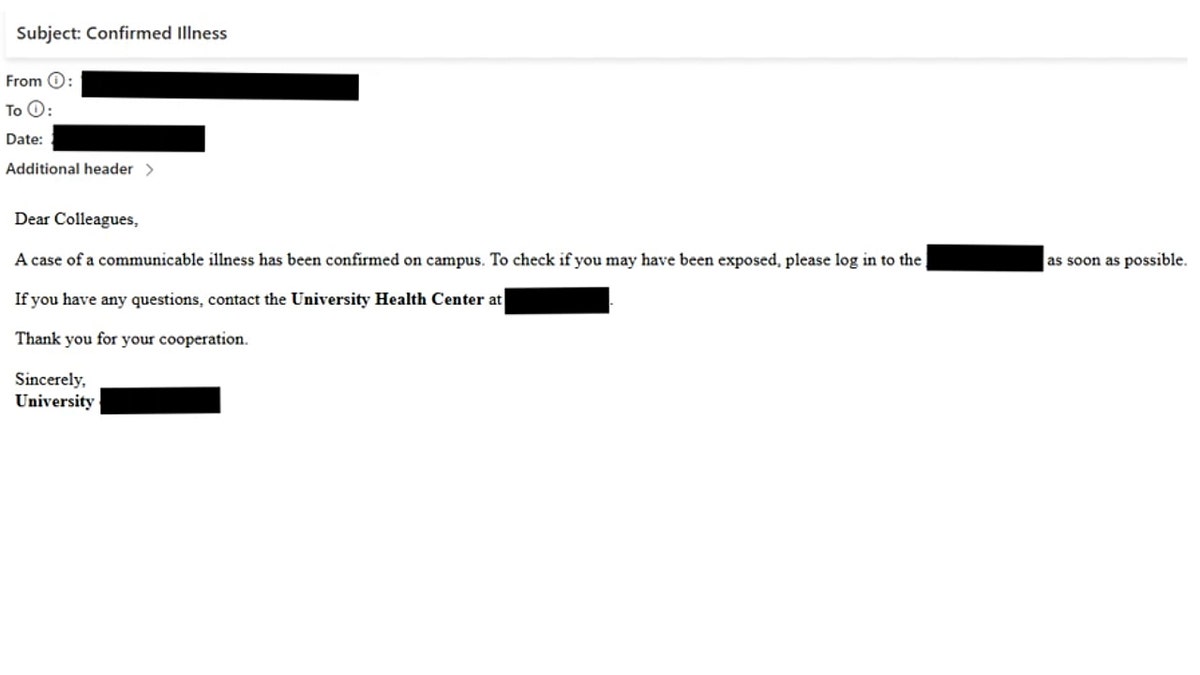
Hackers lure staff with convincing emails that mimic campus alerts or HR updates and steal login details in real time. (Microsoft)
6 ways to stay safe from payroll and phishing scams
Protecting yourself from payroll and phishing scams isn’t complicated. By taking a few careful steps, you can make it much harder for attackers to gain access to your accounts or personal information.
1) Limit what personal information is online
The more information scammers can find about you, the easier it is to craft convincing phishing messages. Services that remove or monitor personal data online can reduce exposure, making it harder for attackers to trick you with targeted emails.
While no service can guarantee the complete removal of your data from the internet, a data removal service is really a smart choice. They aren’t cheap, and neither is your privacy. These services do all the work for you by actively monitoring and systematically erasing your personal information from hundreds of websites. It’s what gives me peace of mind and has proven to be the most effective way to erase your personal data from the internet. By limiting the information available, you reduce the risk of scammers cross-referencing data from breaches with information they might find on the dark web, making it harder for them to target you.
Check out my top picks for data removal services and get a free scan to find out if your personal information is already out on the web by visiting Cyberguy.com.
Get a free scan to find out if your personal information is already out on the web: Cyberguy.com
2) Think before you click
Scammers often send emails that look like they come from your HR department or university leadership, warning about payroll, benefits or urgent issues. Don’t click links or download attachments unless you are 100% sure they are legitimate. Even small mistakes can give attackers access to your accounts.
The best way to safeguard yourself from malicious links is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe.
Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices at Cyberguy.com.

Researchers have discovered that since March 2025, a hacking group known as Storm-2657 has been running “pirate payroll” attacks, using phishing tactics to gain access to payroll accounts. (Javi Sanz/Getty Images)
3) Verify directly with the source
If an email mentions salary changes or requires action, call or email the HR office or the person directly using contact information you already know. Phishing emails are designed to create panic and rush decisions, so taking a moment to verify can stop attackers in their tracks.
4) Use strong, unique passwords
Never reuse passwords across multiple accounts. Scammers often try to use credentials stolen from other breaches. A password manager can help you generate strong passwords and store them securely, so you don’t have to remember dozens of different combinations.
Next, see if your email has been exposed in past breaches. Our No. 1 password manager pick includes a built-in breach scanner that checks whether your email address or passwords have appeared in known leaks. If you discover a match, immediately change any reused passwords and secure those accounts with new, unique credentials.
Check out the best expert-reviewed password managers of 2025 at Cyberguy.com.
5) Enable two-factor authentication (2FA)
Add an extra layer of security by enabling 2FA on all accounts that support it. This means even if someone steals your password, they still can’t log in without a second verification step, such as a code sent to your phone.
6) Regularly check financial and payroll accounts
Even if you follow all precautions, it’s smart to monitor your accounts for any unusual activity. Catching unauthorized transactions quickly can prevent bigger losses and alert you to potential scams before they escalate.
CLICK HERE TO DOWNLOAD THE FOX NEWS APP
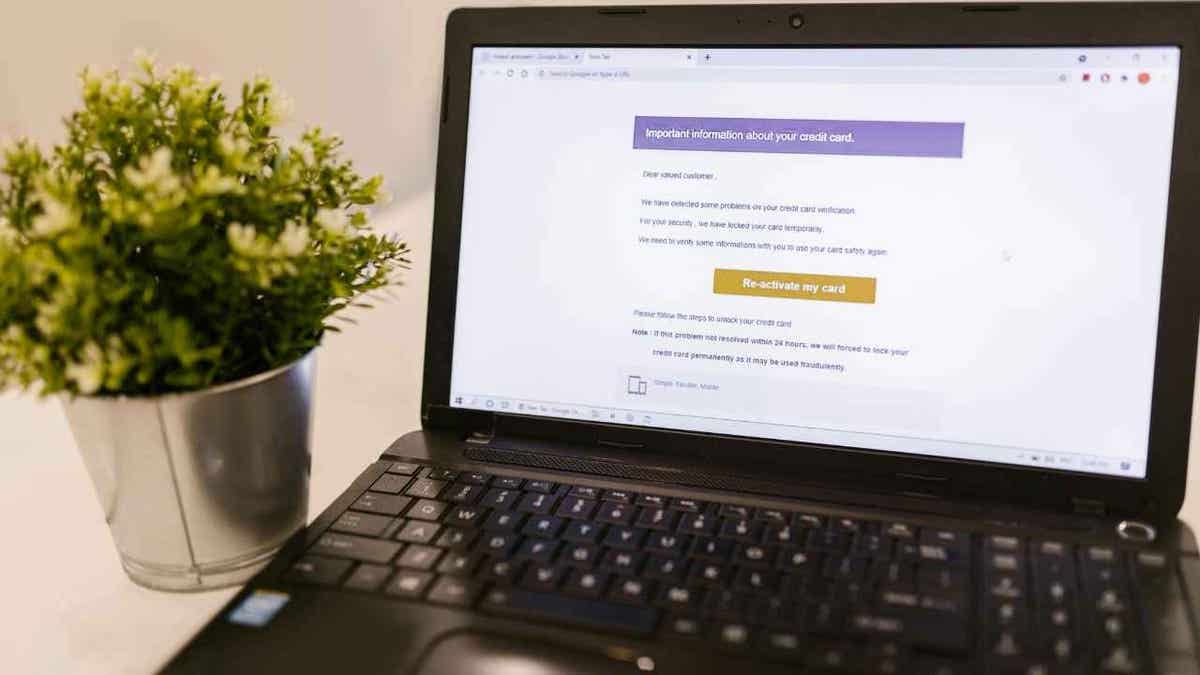
Hackers will reroute payments after gaining access to users’ login information. (Kurt “CyberGuy” Knutsson)
Kurt’s key takeaway
The Storm-2657 attacks show that cybercriminals are targeting trust, not software. Universities are appealing because payroll systems handle money directly, and staff can be manipulated through well-crafted phishing. The scale and sophistication of these attacks highlight how vulnerable even well-established institutions can be to financially motivated threat actors.
How often do you check your payroll or bank accounts for unusual activity? Let us know by writing to us at Cyberguy.com.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide — free when you join my CYBERGUY.COM. newsletter.
Copyright 2025 CyberGuy.com. All rights reserved.
Source link































